Fixing an Android Phone
(is it?)
Case Study:
Someone forgot their Android phone’s passcode and there’s absolutely no way to retrieve it anywhere, no notes, no password manager, no references. Nada. Zilch. Nil. Zero percent that they’d remember it. (or so they said they tried to remember it to no avail)
So they asked your help if you can try to do something about the phone being usable again. They really don’t care much about the data inside. They handed the phone and you see that its a Chinese Android phone with a 6-pin passcode.
What would you do?
Gears turning
Okay so few ideas to bypass it:
- Guess the passcode
- Root the device
- Access the EDL mode
But before digging deep down, we need to know what we’re dealing with.
Identify the device
- Look for any clues physically, maybe reboot the phone or its labeled at the back of the phone. Then match the physical description with the brand of the phone online.
- Take a picture using the camera and check the metadata of the image you just took. It should reveal the model and the version of the device.
- Or maybe just ask the owner I guess? (okay I’m too autistic to ask cuz I know it’ll just take more time to get back and forth with extracting info from them than finding it myself. no judgment pls tnx.)
Btw I identified what the unit was using the EXIF when I took a picture. Model was identified as Vivo 1906 and when I looked it up in teh interwebz the Vivo Y11 search results matched the one I’m working with. Yay.
Hmm… interesting
What got my attention was this device had a ‘Forgot’ button after I tried to enter the passcode. Once pressed, it will go to the next page.
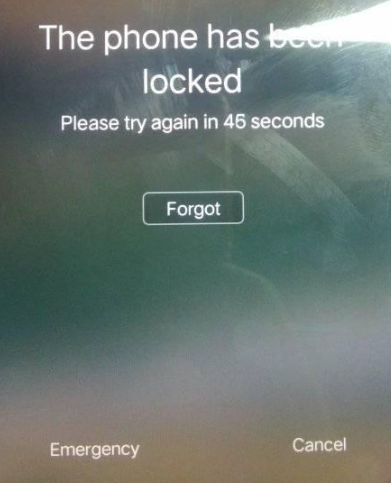
Which is the ‘Identity verification’ asking about what primary school the owner attended and what was the name of their best friend in childhood.
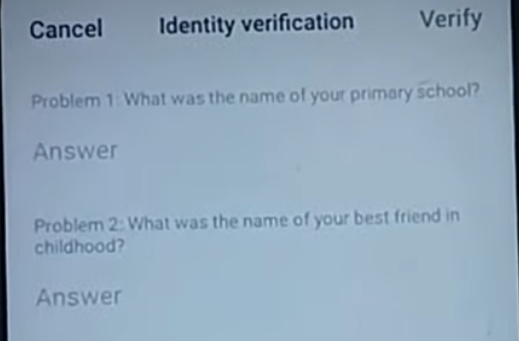
Page had a text field where you have to enter the answer (duhhh) BUT when I tried to long press the field it revealed a ‘Clipboard’ option. I checked what this owner was copying and pasting and saw bunch of data like list of debts with names (?), contact numbers, locations, etc. Definitely useful for the next phase. OSINT.
Option 1 Brute-force the passcode ❌
I think this is the most boring part of hacking that laypeople don’t see. Hackers don’t just happen to access their target’s account. It often involve a lot of data gathering and whole lot of guessing. Lots of password and passcodes are easy to guess since they are directly related to the person of interest: birthdates, anniversaries, pet names, spouse, children, favorite books, bible verses, OR just use the latest rockyou.txt.
Scraping these data off of social media, search engine results, and in general the target’s online presence and footprints is called Open-source Intelligence (OSINT).
I’m in no expert with OSINT framework and my process of doing this is just trying to social media posts and take screenshots lol
Having found the piece of evidence from the clipboard, I was able to look them up in Facebook. My target information were related to anything that is significant to the owner that involves 6 digits.
So my thought process was it might be related to:
- birthdates
- anniversaries, month-saries?
- any other dates that needed to be celebrated
- last 6 digits of the owner’s contact number
- I mean it should be from 000000 to 999999 right? (but anybody ain’t got the time for that lol)
Social Media
- Owner of the phone had themselves as the wallpaper of the phone together with what looks like their significant other (SO), I tried to reverse image search but no results were found.
- Pivoting to the names in the clipboard history, I managed to locate the owner and their active accounts. Was also able to match the images in the wallpaper to these person’s posts. So it solidified the findings.
Well actually, I got all the accounts that has been created with this person’s name. (seems like this person does had a sign of being forgetful, hmm… I mean no judgment btw juuuust observing)
- Looked out for any publicly posted greetings like ‘happy birthday’, ‘happy anniversary’ with all the accounts I found with the owner and their SO.
- Read through posts to find where they exactly live to list down possible answers for the secret questions.
- Created a list of all the data I had including the screenshots.
Was feeling hopeful really. I was successful gathering all the data (I think I was) but I guess I still missed a lot since those were not the combination I’m looking for.

Noped out after that. Moved on to other options.
Option 2 Root the device using exploit ❌
Since the model was old enough to be in elementary school (released in 2018-2019) I thought rootkits should be available in XDA or other forums but I didn’t bother to check it out. Not yet.
Option 3 Entering EDL Mode ✅
This got me curious since almost all guides and tutorials to bypass a phone often involved prying in the motherboard and tinkering the ‘Test Points’.
Now again, I’m no expert here. But I learned a few terms along the way:
EDL (Emergency Download Mode): EDL is a special mode on Android devices that lets you recover or unbrick your device by flashing firmware directly to the phone’s storage. It’s like a rescue mode that bypasses the regular boot process.
Testpoints: Testpoints are small contact points on a device’s motherboard that can be shorted to trigger specific hardware states, like entering EDL mode. They’re often used in advanced repair or unbricking procedures.
EDL mode is there so peeps can save the phone by reinstalling firmware (reflashing) by modifying the partitions or you could it use to tamper with userdata.

So basically, you need to access these testpoints to enter EDL mode. To do that you need:
- computer,
- the software needed to read and access the data via the computer,
- the device driver to interpret the data from the android phone, and a
- power and data cable to connect the phone, and lastly
- patience. Lotta patience.
- also snacks.
Here’s what I did:
- Opened the back and unscrewed the panel covering the ribbon as seen below

- Removed the foam and we can see two other gold circles underneath.

-
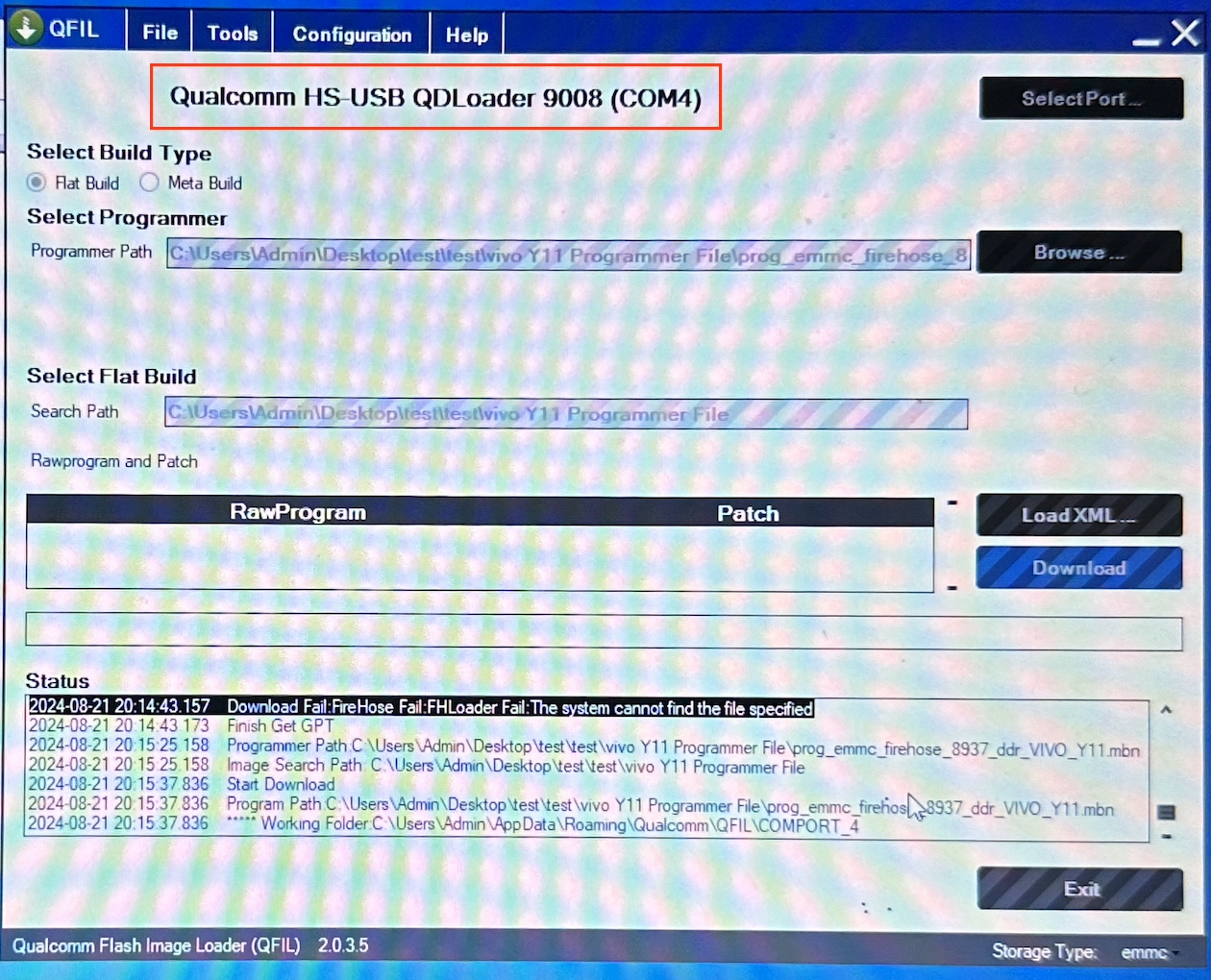
Prepped up the computer by installing QFIL and QPST and grabbing the correct Firehose build.
-
Downloaded and installed the USB Driver for Qualcomm.
-
Run the QFIL.
-
Now for the most tricky part, using a tweezer try to press the gold dots as seen below

- If all was setup properly, QFIL should able to read the device (apologies for the potato quality)
- If all goes smooth, it should prompt the Partition Manager.
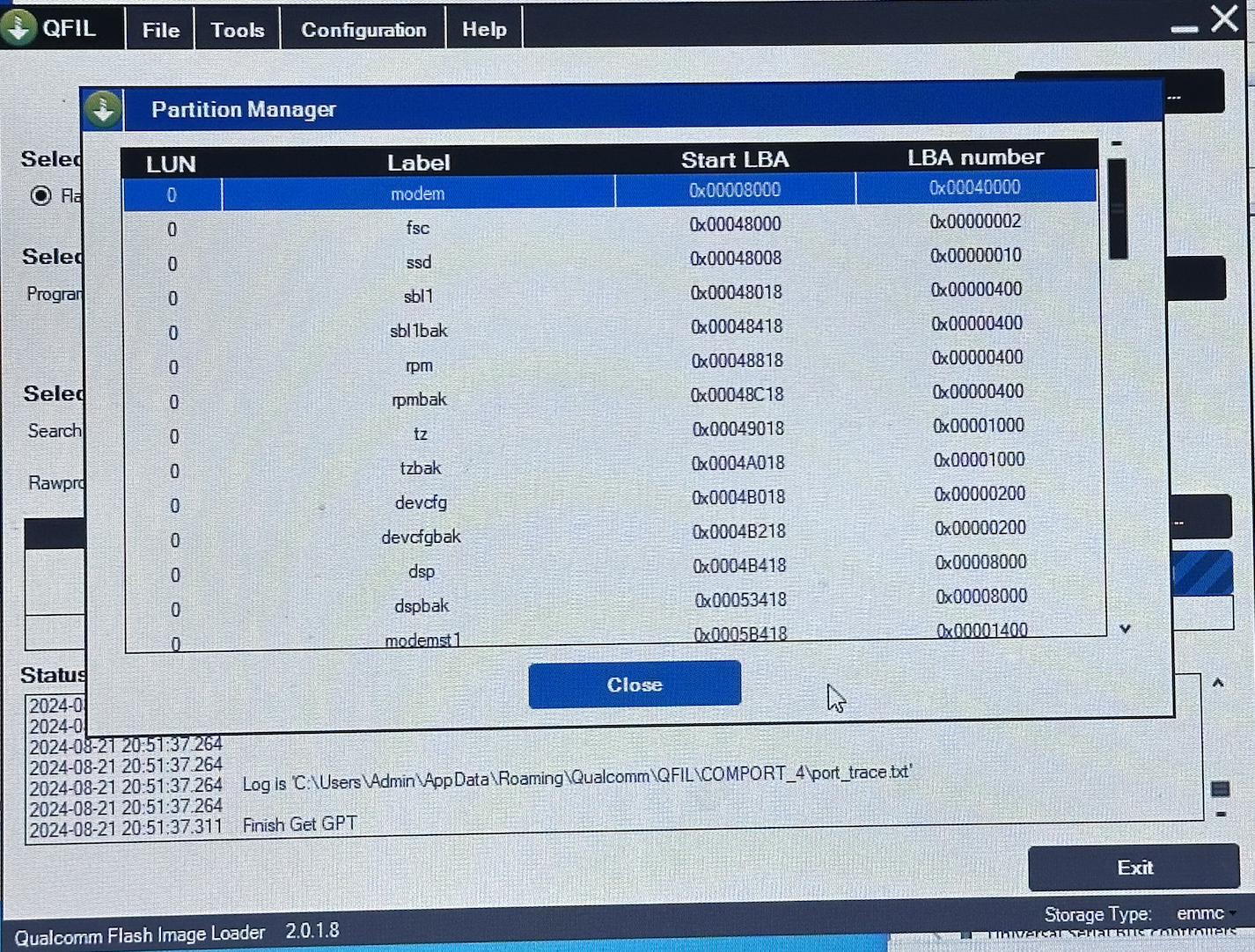
And…. scrolling down…

what’s this…?
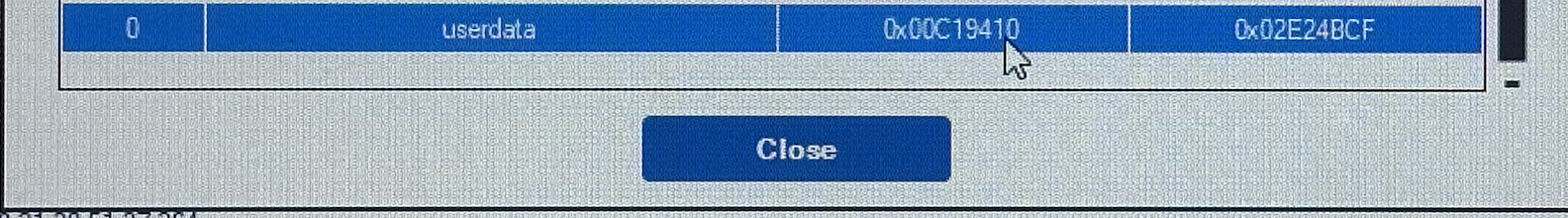
Welp, it’d be a shame if somebody…
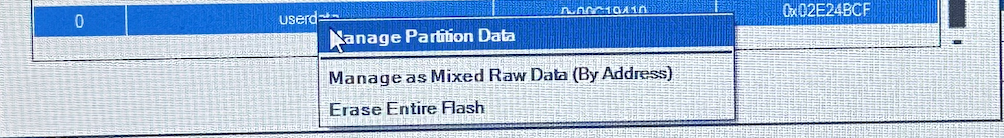
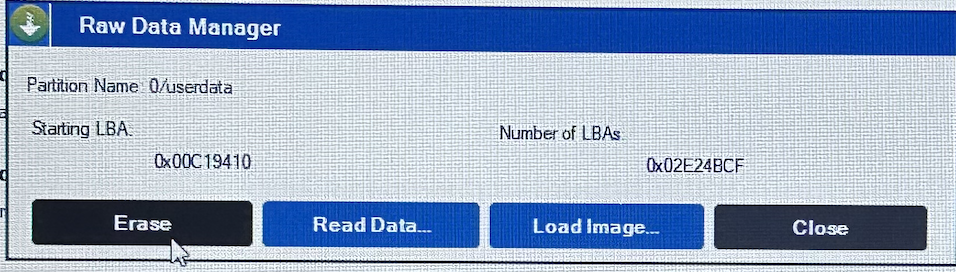
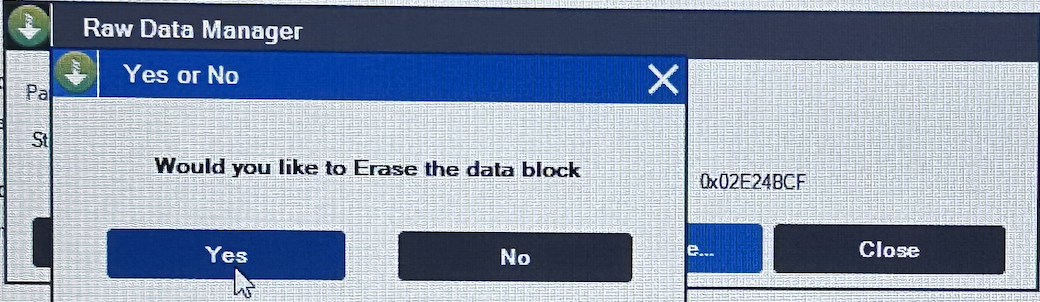
…erased it.
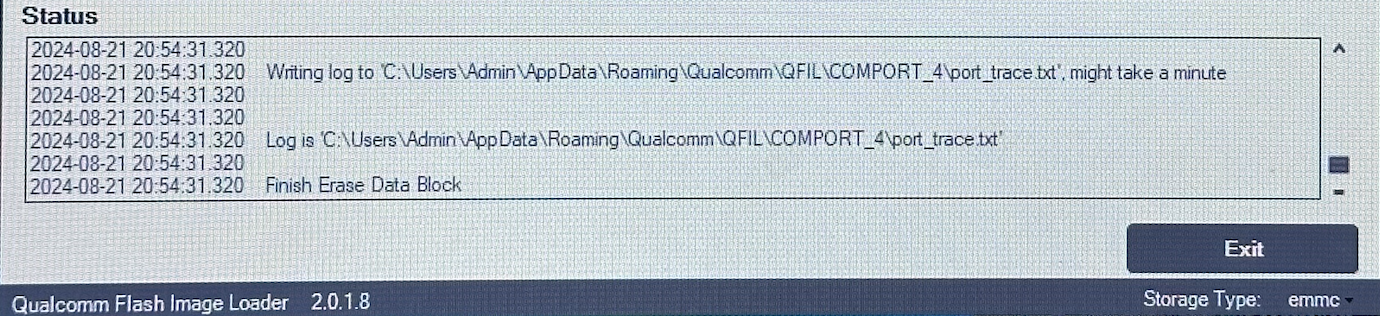

- Exit the program, put back the display ribbon, and wait for the device to boot up. It should be able clear all data without asking for any codes.
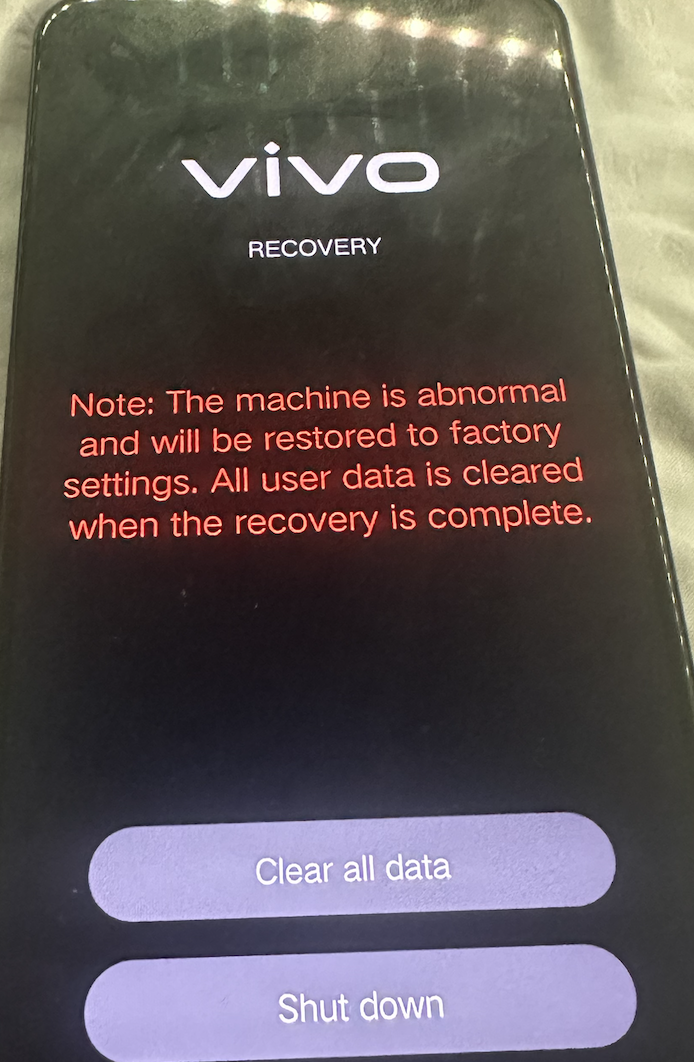
- And there you have it. Bypassed the passcode and was able to reset the phone.
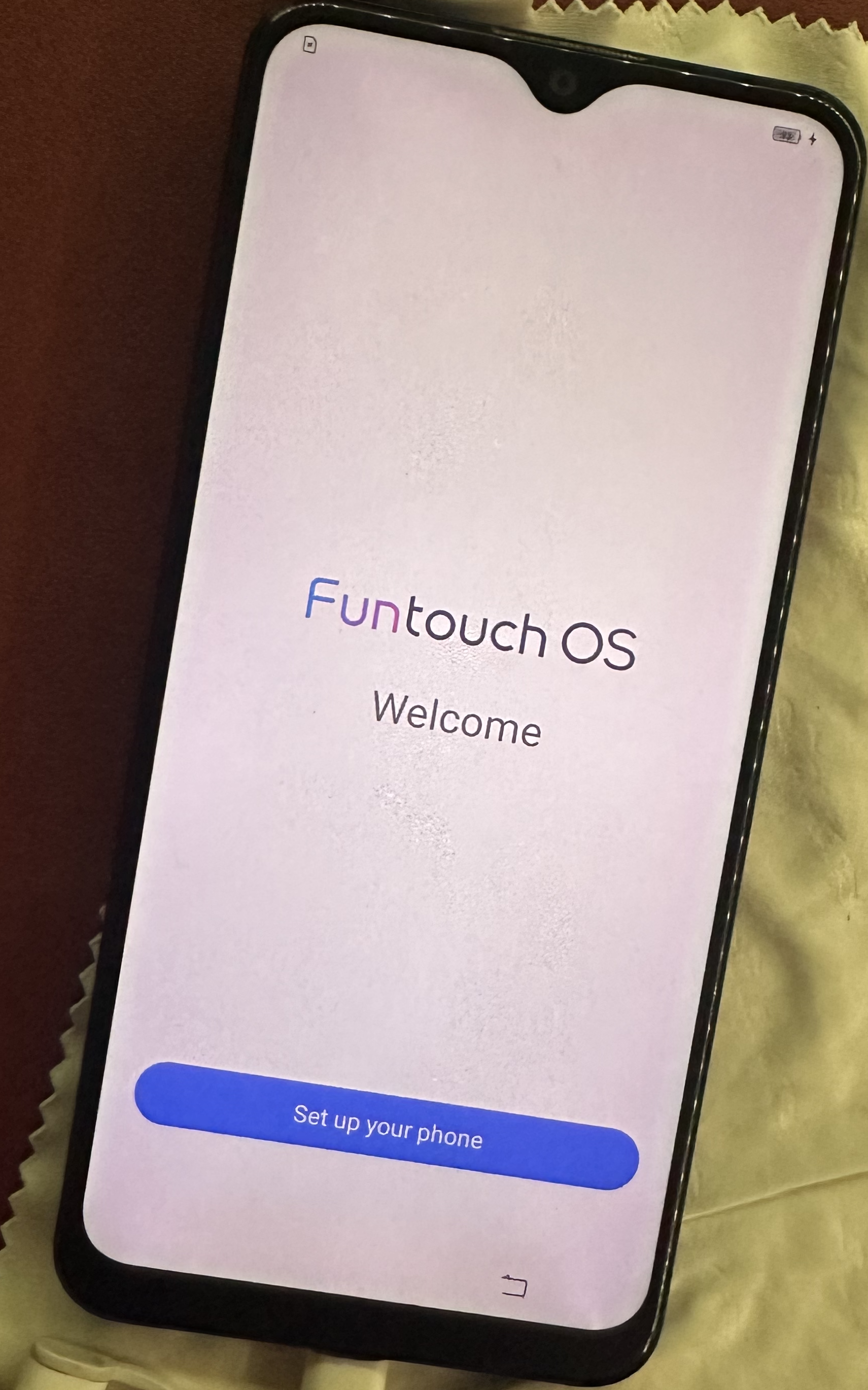
-
???
-
Profit
tl;dr
Owner gave me their phone to remove the security passcode, didn’t care about the data. Tried to guess the PIN, didn’t work. Accessed the EDL and was able to reformat the device. Yay.
DISCLAIMER:
This tutorial is provided for educational purposes only. The methods and instructions outlined here should only be used on devices you own or have explicit permission to modify. Unauthorized access or tampering with a device’s software can violate terms of service, void warranties, and potentially render the device unusable. The author is not responsible for any damage, data loss, or legal consequences resulting from the use of this tutorial. Proceed with caution and at your own risk.