Written
on
Phishing Email - Email from Paypal (Let's Defend)
Challenge Write-up (Easy)
Lessons Learned:
To quickly analyze a phishing email without using any email application.
The Challenge:
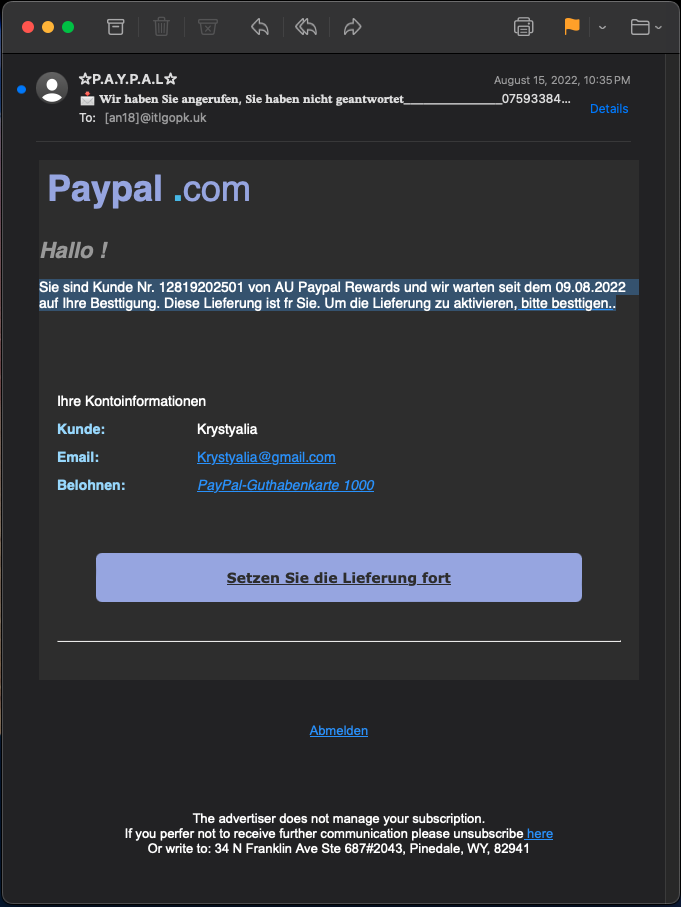
Your email address has been leaked and you receive an email from Paypal in German. Try to analyze the suspicious email.
- What is the return path of the email?
- Method: Open the .eml file with any text editor and it will dump all the details including the email header.
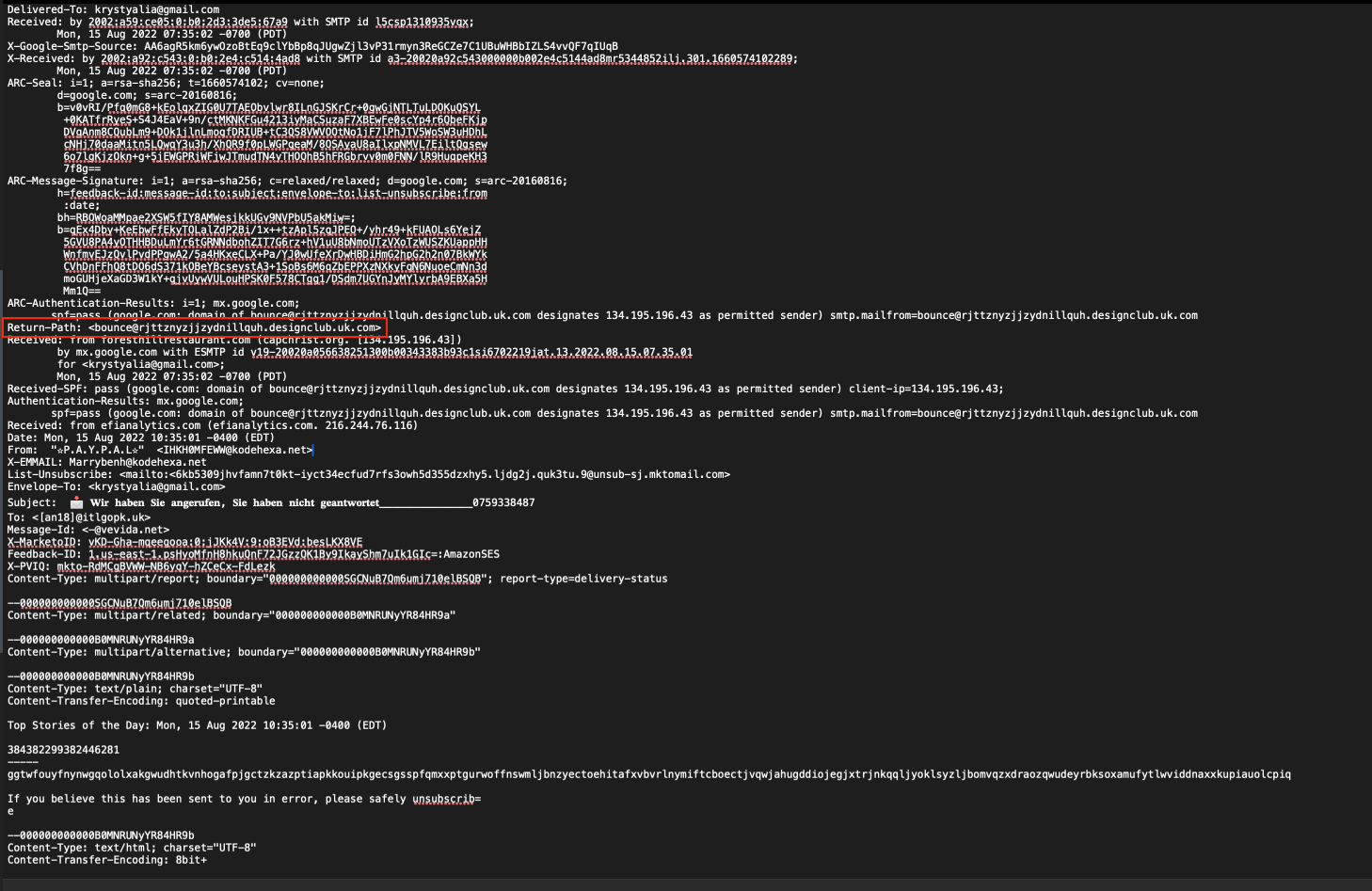
- Answer: “bounce[at]rjttznyzjjzydnillquh[dot]designclub[dot]uk[dot]com”
- What is the domain name of the url in this mail?
- Method: Analyze the contents of the email and there should be a link stated around the body of the message.

- Answer: “storage.googleapis.com”
- Is the domain mentioned in the previous question suspicious?
- Method: Check various sites for domain reputation. In this case, VirusTotal. Enter the full URL found in the message in Q3 and wait for the result.
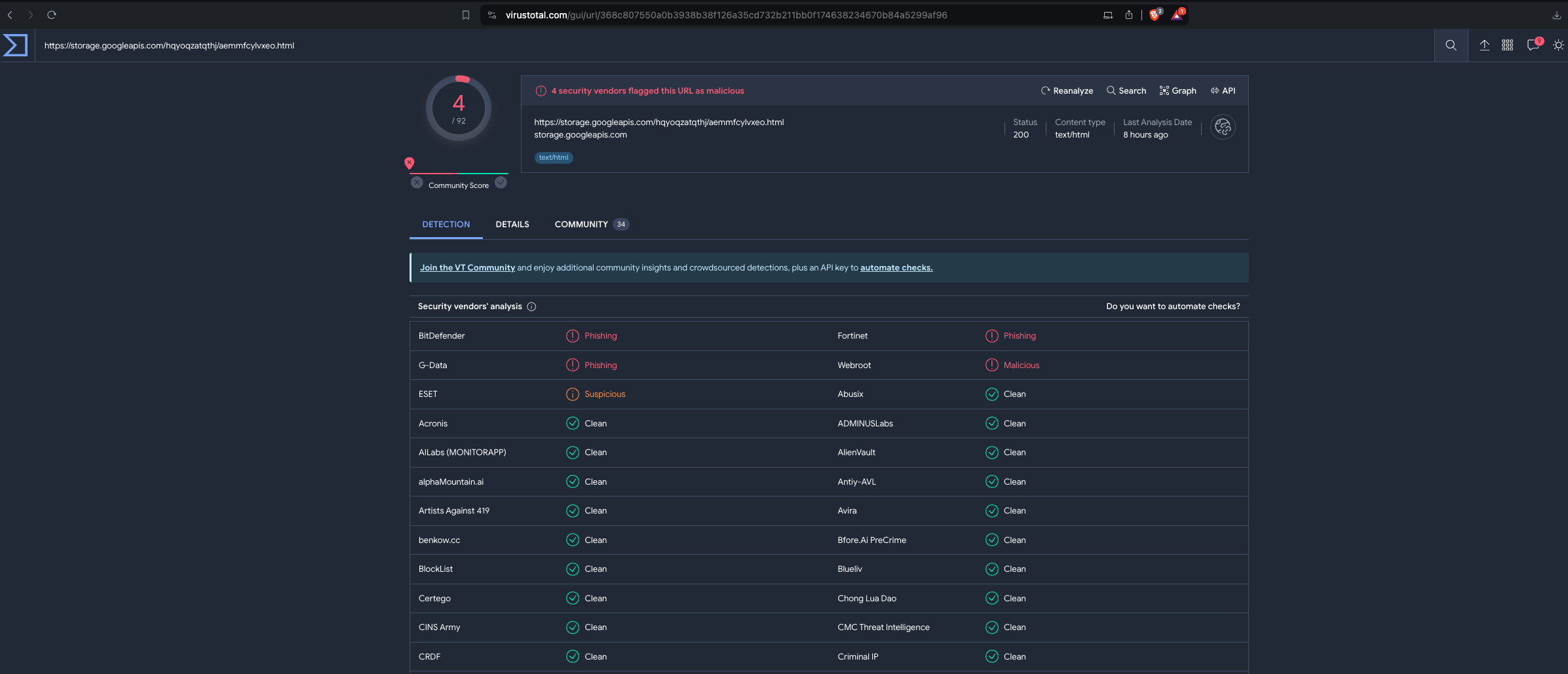
- Answer: “Yes”
- What is the body SHA-256 of the domain?
- Method: In VirusTotal, under Details tab.
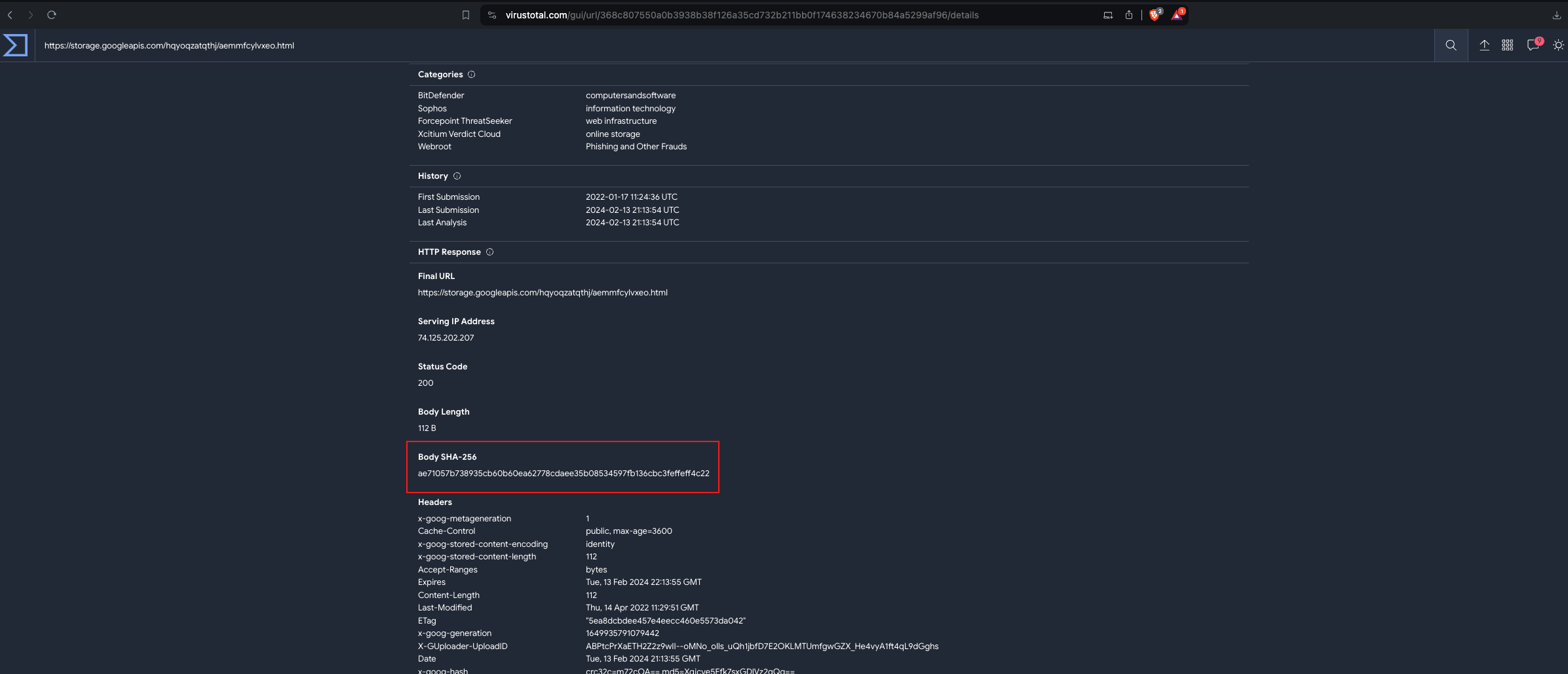
- Answer: “ae71057b738935cb60b60ea62778cdaee35b08534597fb136cbc3feffeff4c22”
- Is this email a phishing email?
- Method: Analyzing the structure of the email, the common indicators would be:
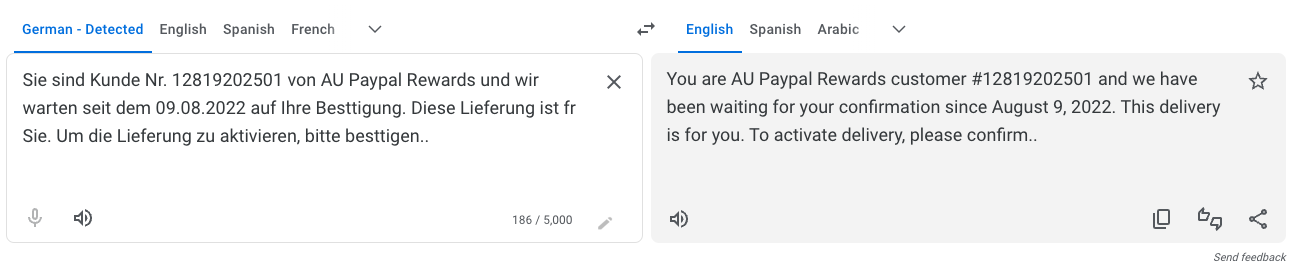
- The urgency - “we have been waiting for your confirmation since August 9, 2022.”
- Content - Paypal logo, German language, the link.
- VirusTotal tagged it as such.
- Answer: “Yes”