Cybersecurity - The Bigger Picture (4/n)
(I guess)
Infinity and beyond
Okay now, what. You have computers that know how talk to each other. When can I watch cute animals doing stuff?
Alright calm down, still have a lot to discuss.
Remember the part where we mentioned about the tricks inside NCP? The address one? You see, this corresponds to your network address. It is your identity within the network. Without it, traffic will not follow to and from your computer. (Its one of the basics of troubleshooting network issues — always check first if you have IP address!)
IP address can be used to locate and connect to other machines within the network. Much like using telephone number. But do you really have the capacity to memorize all IP addresses? So going back to the telephone analogy, they basically created some sort of a telephone book to make it easier to memorize. Instead of trying to remember numbers like a robot, you’ll just have to think about names! (Now we’re making progress!).
So they setup this machine containing all IP addresses and their equivalent names whatever they set, kinda goes something like this:
Alice: I want to reach out Bob’s laptop: BOB.PC
Network: I gots this. * goes to DNS server to check for the files *
Network: Found it! Here you go. He’s on 192.168.1.3.
Alice: k.
Don’t mind Alice’s attitude.

But you also gotta think this is just a small scale. If we’re going to expand this addressing issue to a global scale, how will this work out? Welp, let’s form another group again.
- Global Bossman — Internet Assigned Numbers Authority (IANA).
- Regional Bossmans
- ARIN (American Registry for Internet Numbers): Serves North America, parts of the Caribbean, and sub-Saharan Africa.
- RIPE NCC (Réseaux IP Européens Network Coordination Centre): Serves Europe, the Middle East, and Central Asia.
- APNIC (Asia-Pacific Network Information Centre): Serves the Asia-Pacific region.
- LACNIC (Latin America and Caribbean Network Information Centre): Serves Latin America and the Caribbean.
- AFRINIC (African Network Information Centre): Serves Africa.
So you need something about a certain IP address you just gotta check their records.
Emailing systems also kind of worked the same way using the SMTP to communicate.
Little bit of trivia: When Steve Jobs and Bill Gates saw the Alto Computer (created by Xerox PARC) they thought of an idea to create the graphical user interface (GUI) which later became Apple’s personal computer: Apple II. Alto computer also influenced Microsoft when creating their software products. So now we have operating systems: Apple DOS and MS-DOS. (Yup, Microsoft at that point only sold products, not hardware). In order to use these machines you need to learn and memorize command lines (‘whoami’, ‘dir’, ‘sudo rm -rf /’, sounds familiar?).

There’s just one more thing. You are doing these typings, these networkings, etc. like you’re in a matrix. It’s all just texts and lines, no other colors, and stuff. (I know!, eek). But get this, in 1983, the same year, hell even the same month, no, 3 days after the internet was created, Apple launched their first GUI-based Personal Computer: Apple Lisa. It basically replaced everything on your desk which is similar in today’s computers. This computer is running Lisa OS featured a graphical user interface (GUI) and introduced several innovative features for its time, such as preemptive multitasking and a document-centric approach to computing. A year later, they’ve created a new and much affordable PC, the Macintosh using Apple System OS (which became Mac OS).

Microsoft released their very own OS, Windows 1.0 in 1985 for IBM PCs. Windows and Macintosh were pretty much the same at that point with a limited specs to store memory, you’re lucky if you can type in a secured password.
Trivia: Macintosh was named after the type of apple called “McIntosh”. They just changed it to avoid legal repercussions.
Microsoft named their operating system as Windows, because when a user logged in on version 1.0 they’ll see a Windowed applications!
Fast forward in 1988, Steve Jobs invented a new computer called NeXT. This machine will later on be used by Sir Tim Berners-Lee, the inventor of Web with Hypertext Markup Language (HTML) as its publishing language, also including the Web browser. But the usage of web server back then was not for funny gifs, just for reading research documents.
Trivia: NeXT was bought by Apple and then later on became the basis for Mac OS X and iOS!
So then came 1995, you can now browse websites and other stuff since operating systems this time have their own web browsers pre-installed as we have today. But over the course of these events. Security issues were also growing.
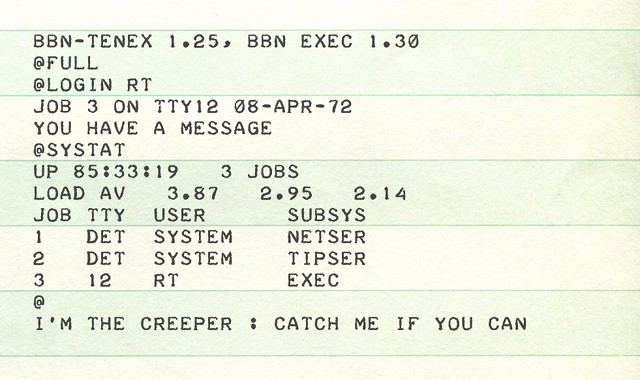
In 1983 was when we first heard the term, “computer virus”. It was injected into a Unix command hidden in a legitimate program on a floppy disk. Once the floppy disk was inserted into a mainframe, it will allow anyone to gain control of a mainframe computer. Earlier versions of malware were also recorded like “Creeper Virus” (1971), the “Elk Cloner” infecting Apple II computers (1981).
If there’s a virus, there’s also anti-virus. Endpoint protection at that time looks like very much use signature-based approach and pretty much reactive and as we’ve learned from the previous posts, your computer will only get infected if you use infected floppy disks or other removable storage media. So what about network intrusions?
Okay. So there’s this one guy connected to the internet back in 1988. He got curious and tried to map the whole internet. You gotta take note this is early years of internet its kind of small at that point so its fairly doable.
- So he created a program and when that arrives on a particular computer it will exploit it and report it back to him as online.
- If the program finds another machine within the network it will also jump on the other computers.
- But he also thought, what if people shield their machines out we won’t have an accurate number of machines online, right?
- So he created a condition which basically reinfects other machine even if it was already infected by creating and running the program again and again. Boom. It became Coco Crunch.
And that’s the story of Morris Worm. I guess.

Later on, network-based system to monitor and inspect traffic were developed. Earlier versions of network firewall were called Packet Filters/Packet Filter Firewalls. It just read traffic and determines what action should be done depending on how the user set its access-control list. Both of these security mechanisms (AVs and Firewalls) will now evolve into a much more complex tools as we’ve seen today.
tl;dr
Computers back then didn’t think about security. Got rekt. Then react. Shrugs.
Disclaimer: All of these analogies are gross simplification. Implementations have long been changed.